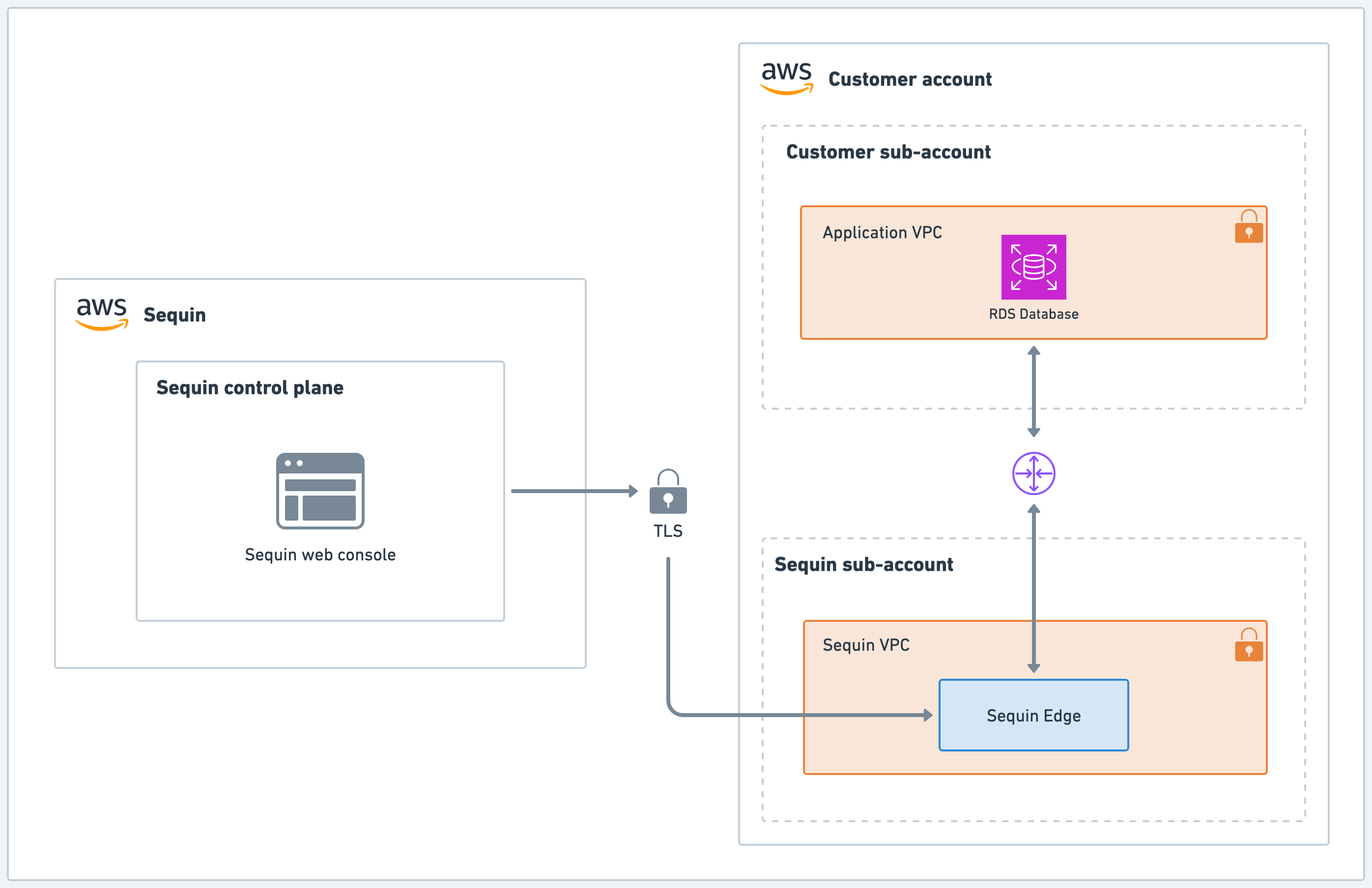
Architecture
In this setup, the Sequin “data plane” is installed inside a Sequin-operated sub-account in your AWS organization. We provision and manage the necessary streaming components (via Terraform and ECS) within that sub-account. We deploy two Sequin instances (on ECS Fargate) in active-passive mode, spread across different availability zones for high availability. We’ll also provision a small RDS (Postgres) instance and a Redis service to support your streaming infrastructure. All core processes run in the dedicated sub-account, which is part of your AWS organization. Sequin does not gain access to your other accounts or organization-level settings. Meanwhile, the “control plane” — including the Sequin API and web app — remains external.